Organizations exploring options to reduce the cost of IT security investments while maintaining the confidentiality, integrity and availability of IT resources. Microsoft clients with E5 license can evaluate the below 16 functional domains to utilize the security use-cases and replace security vendors. However, if customer’s have unique requirements that are achievable only with marketplace security products should continue to leverage other security solutions.
1. Single Sign-on (SSO)
Single sign-on means a user doesn’t have to sign in to every application they use. The user logs in once and that credential is used for other apps too. You can find your apps at: https://myapps.microsoft.com. This flowchart helps you decide which single sign-on method is best for your situation.

With Azure AD Free end users who have been assigned access to SaaS apps can get unlimited SSO access to cloud apps. On-premises applications require Azure AD Application Proxy or secure hybrid partnerships integrations available with Azure AD P1 and P2.
2. Multi-Factor Authentication (MFA)
Multi-factor authentication is a process where a user is prompted during the sign-in process for an additional form of identification, such as to enter a code on their cellphone or to provide a fingerprint scan.
Basic multi-factor authentication features are available to Microsoft 365 and Azure Active Directory (Azure AD) administrators for no extra cost. If clients want to upgrade the features for admins or extend multi-factor authentication to the rest of your users, you can purchase Azure Multi-Factor Authentication in several ways.
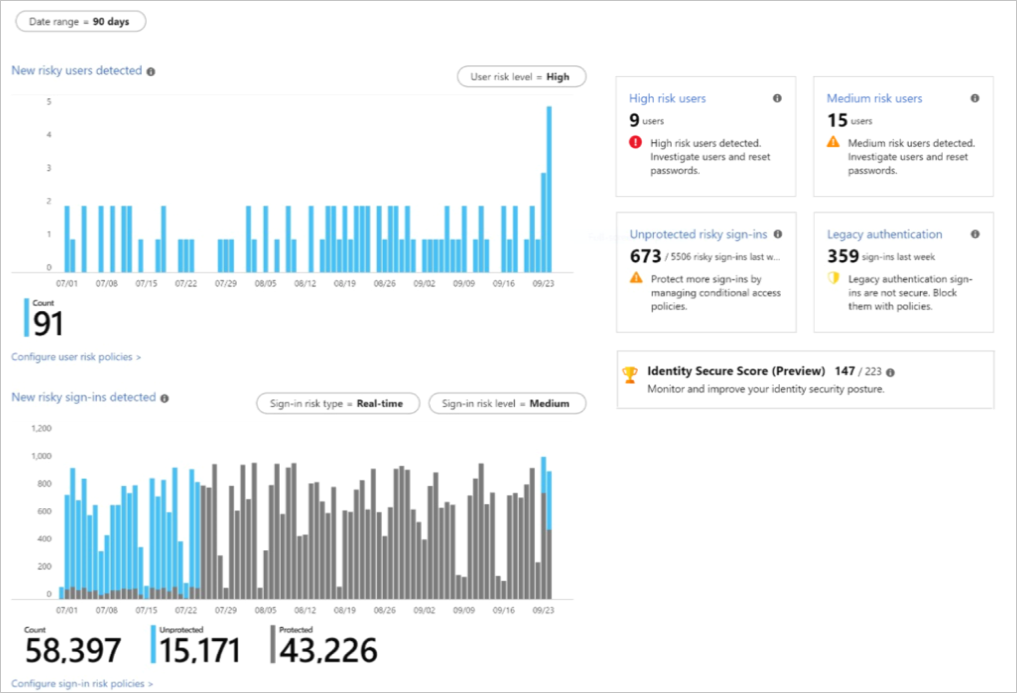
3. Identity Protection
Identity Protection is a tool that allows organizations to accomplish three key tasks:
- Automate the detection and remediation of identity-based risks.
- Investigate risks using data in the portal.
- Export risk detection data to third-party utilities for further analysis.
4. Privileged Access Management (PAM)
Privileged Identity Management provides time-based and approval-based role activation to mitigate the risks of excessive, unnecessary, or misused access permissions on resources that you care about. Here are some of the key features of Privileged Identity Management:
- Provide just-in-time privileged access to Azure AD and Azure resources
- Assign time-bound access to resources using start and end dates
- Require approval to activate privileged roles
- Enforce multi-factor authentication to activate any role
- Use justification to understand why users activate
- Get notifications when privileged roles are activated
- Conduct access reviews to ensure users still need roles
- Download audit history for internal or external audit

5. Data Loss Prevention (DLP)
Microsoft DLP helps to identify sensitive information across many locations, such as Exchange Online, SharePoint Online, OneDrive for Business, and Microsoft Teams. The DLP policies prevent the accidental sharing of sensitive information, Monitor and protect sensitive information in the desktop versions of Excel, PowerPoint, and Word. Likewise to view DLP reports showing content that matches your organization’s DLP policies.

6. Data Encryption
Encryption is an important part of your file protection and information protection strategy. The technologies for data encryption used by Microsoft are
- BitLocker can be used on client machines, such as Windows computers and tablets
- Distributed Key Manager (DKM) in Microsoft datacenters.
- Customer Key for Microsoft 365
- TLS for files in transit
- Office 365 Message Encryption with Azure Rights Management, S/MIME, and TLS for email in transit
- Teams uses TLS and MTLS to encrypt instant messages. Media traffic is encrypted using Secure RTP (SRTP). Teams uses FIPS (Federal Information Processing Standard) compliant algorithms for encryption key exchanges.
7. Information Protection
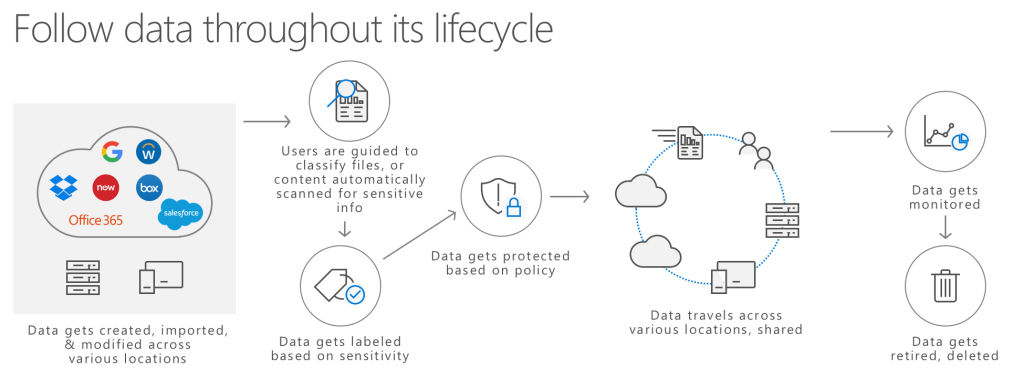
Microsoft Information Protection (MIP) to help you discover, classify, and protect sensitive information wherever it lives or travels.
Microsoft Information Protection solutions help you protect sensitive data throughout its lifecycle – across devices, apps, cloud services and on-premises.
| M365 Information Protection | Capabilities |
| Classification & labeling of sensitive data | Manual classification and labeling in Office 365 (Exchange Online, SharePoint Online, OneDrive for Business) Automated classification and labeling in Office 365 (Exchange Online, SharePoint Online, OneDrive for Business) Manual classification and labeling beyond Office 365 locations (cloud services, on-premises) Automated classification and labeling beyond Office 365 locations (cloud services, on-premises) Native end-user labeling experiences in Office apps |
| Encryption & rights-based restrictions | Add ad-hoc protection to Office documents Encrypt emails to internal or external recipients |
| Data Loss Prevention (DLP) | Block sharing of sensitive information in Office 365 (Exchange Online, SharePoint Online, OneDrive for Business) |
| Cloud App Security | Protect data in 3rd-party SaaS apps and cloud services |
| Windows Information Protection | Prevent copying and sharing of data from a business location to a non-business location on Windows 10 devices |
| Monitoring, analytics, remediation | Track and revoke protected documents Analytics on classified, labeled and protected documents (endpoints, sensitivity, users) |
8. Data Classification
Microsoft data classifications has flexible options listed below
- Automatic classification – Policies can be set by IT Admins for automatically applying classification and protection to data
- Recommended classification – Based on the content you’re working on, you can be prompted with suggested classification
- Manual reclassification – Users can override a classification and optionally be required to provide a justification
- User-driven classification – Users can choose to apply a sensitivity label to the email or file they are working on with a single click
Data classification will scan your sensitive content and labeled content before you create any policies. This is called zero change management. This lets you see the impact that all the retention and sensitivity labels are having in your environment and empower you to start assessing your protection and governance policy needs.
9. Data Governance
Microsoft Information Governance (sometimes abbreviated to MIG) capabilities to govern your data for compliance or regulatory requirements. Few capabilities that Microsoft data governance will solve are
- Retain or delete content with policy management and a deletion workflow for email, documents, instant messages, and more
- Bulk-import PST files to Exchange Online mailboxes to retain and search email messages for compliance or regulatory requirements
- Import, archive, and apply compliance solutions to third-party data from social media platforms, instant messaging platforms, and document collaboration platforms
- Retain mailbox content after employees leave the organization
- A single solution for email and documents that incorporates retention schedules and requirements into a file plan that supports the full lifecycle of your content with records declaration, retention, and disposition
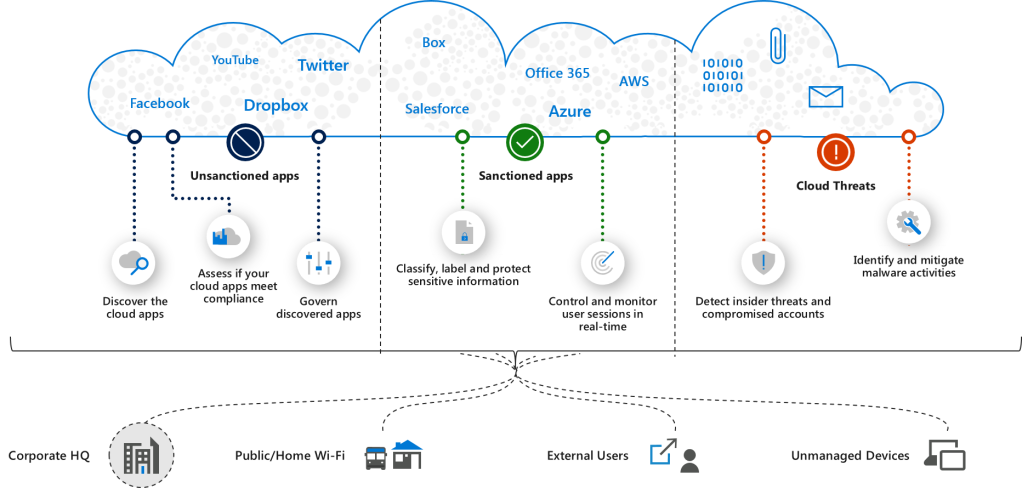
10. Cloud Access Security Broker (CASB)
Microsoft Cloud App Security is a Cloud Access Security Broker that supports various deployment modes including log collection, API connectors, and reverse proxy. It provides rich visibility, control over data travel, and sophisticated analytics to identify and combat cyber threats across all your Microsoft and third-party cloud services.
11. Key Management
The Key Management Service (KMS) is an activation service that allows organizations to activate systems within their own network, eliminating the need for individual computers to connect to Microsoft for product activation. It does not require a dedicated system and can be easily co-hosted on a system that provides other services.
Azure Key Vault is a tool for securely storing and accessing secrets. A secret is anything that you want to tightly control access to, such as API keys, passwords, or certificates. A vault is a logical group of secrets.
12. Mobile Application Management
Intune mobile application management refers to the suite of Intune management features that lets you publish, push, configure, secure, monitor, and update mobile apps for your users.
MAM allows you to manage and protects your organization’s data within an application. With MAM without enrollment (MAM-WE), a work or school-related app that contains sensitive data can be managed on almost any device, including personal devices in bring-your-own-device (BYOD) scenarios.
13. Secure Email Gateway
Email has become a reliable and ubiquitous communication medium for information workers in organizations of all sizes. Messaging stores and mailboxes have become repositories of valuable data. It’s important for organizations to formulate messaging policies that dictate the fair use of their messaging systems, provide user guidelines for how to act on the policies, and where required, provide details about the types of communication that may not be allowed.
Exchange Online Protection (EOP) is the cloud-based filtering service that helps protect your organization against spam and malware. EOP is included in all Microsoft 365 organizations with Exchange Online mailboxes.

Office 365 Advanced Threat Protection (ATP) safeguards your organization against malicious threats posed by email messages, links (URLs) and collaboration tools.
14. Endpoint Detection and Response (EDR)
Microsoft Defender ATP is a holistic, cloud delivered endpoint security solution that includes risk-based vulnerability management and assessment, attack surface reduction, behavioral based and cloud-powered next generation protection, endpoint detection and response (EDR), automatic investigation and remediation, managed hunting services, rich APIs, and unified security management.
Microsoft Defender Advanced Threat Protection requires one of the following Microsoft Volume Licensing offers:
- Windows 10 Enterprise E5
- Windows 10 Education A5
- Microsoft 365 E5 (M365 E5) which includes Windows 10 Enterprise E5
- Microsoft 365 E5 Security
- Microsoft 365 A5 (M365 A5)
Microsoft Defender ATP support other operating systems such as Android, MacOS, Linux
The Microsoft Defender ATP agent depends on the ability of Microsoft Defender Antivirus to scan files and provide information about them. When Microsoft Defender Antivirus is not the active antimalware in your organization and you use the Microsoft Defender ATP service, Microsoft Defender Antivirus goes on passive mode.
15. Endpoint Protection (EPP)
Microsoft Endpoint Protection let you manage the following Microsoft Defender policies for client computers:
- Microsoft Defender Antimalware
- Microsoft Defender Firewall
- Microsoft Defender Advanced Threat Protection
- Microsoft Defender Exploit Guard
- Microsoft Defender Application Guard
- Microsoft Defender Application Control
Endpoint Protection in Configuration Manager lets you to manage antimalware policies and Windows Firewall security for client computers

16. Anti-phishing
Phishing is an email attack that tries to steal sensitive information in messages that appear to be from legitimate or trusted senders. Microsoft Exchange Online Protection (EOP) and the additional features in Office 365 Advanced Threat Protection (Office 365 ATP) can help protect organization from phishing threats.
Microsoft also has other security capabilities such as security score, host firewalls, host intrusion prevention solution, threat intelligence, security graph API and constantly committed to enhance the security features in its M365 platform and services.
Also read






Leave a comment