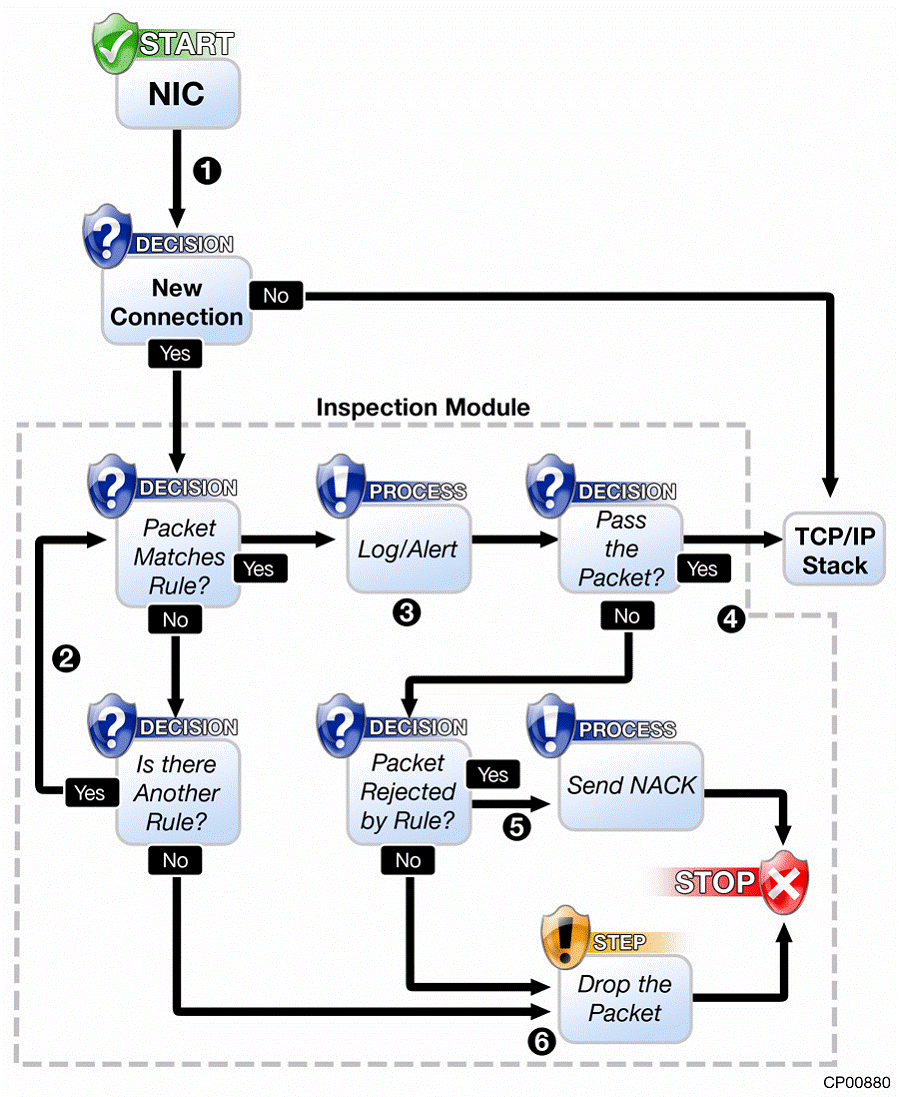
The Security Gateway integrates both network-level and application level protection by combining Stateful Inspection and Application Intelligence. All inbound traffic is routed through the Security Gateway, as this is the logical place for active defenses to reside. System resources and processing time are saved by processing packets in an operating system’s kernel. Applications and processes in the kernel layer suffer little, if any, performance degradation, and can support data throughput rates ranging in the multi gigabits. The Security Gateway kernel is placed between NICs and the TCP/IP stack, solving the problem of protecting the TCP/IP stack itself.
Packet Flow Through the INSPECT Engine If packets pass inspection, the Security Gateway passes the packets through the TCP/IP stack and to their destination. Packets pass through the NIC, to the Inspection Module, and up through the network stack. Some packets are destined for an operating system’s local processes. In this case, the Inspection Module inspects the packets and passes them through the TCP/IP stack. If packets do not pass inspection, they are rejected or dropped and logged, according to rules set in the Check Point Rule Base. (The Rule Base is a collection of individual rules that determine your Security Policy.)
Packets are not processed by higher protocol-stack layers, unless the Security Gateway verifies that they comply with Security Policies.





Leave a comment